Medtech Cyber-Incidents: A Costlier Problem Than You Think
By Elliot Turrini and Ben Locwin

Harnessing advanced computing technologies — e.g., “artificial intelligence (AI), faster and smaller computing hardware, computing-driven robotics, augmented/virtual reality, and Internet of Things (IoT)” — gives medtech companies almost unlimited profit opportunities, as our May 4, 2022, article explained.
Our article warned that this opportunity comes with “almost unlimited liability” from cyber-attacks. While medtech companies have heard general cyber-attack warnings like this for years, many are still woefully underprepared — particularly because they materially underappreciate the financial danger of cyber-attacks. This happens largely because of the cognitive bias “positive illusion,” a systemic decision/judgment error of “unrealistic optimism about the future,” that we addressed in our November 11, 2020 article about medtech and cognitive biases.
Hoping to help medtech companies leveraging advanced computing technologies better mitigate their cyber risks, this article has three parts:
- It details the complex, business-threatening cyber risks that digital medtech companies face;
- It discusses the four factors exacerbating these already business-threatening risks; and
- It provides a chilling, realistic cyber-attack scenario that brings it all together.
Medtech’s Complex, Business-Threatening Risks
To help medtech companies understand their business-threatening cyber risks, we offer an infographic and related taxonomy classifying cyber risks into five categories of harmful events — operational interference, device problems, data breaches, financial and IP theft, and compliance and sales issues — and showing that one or more harmful events can produce one or more types of financial harm: lost sales, customers, investors, and partners; regulatory costs; extortion payments; financial theft; and investigation and remediation costs.
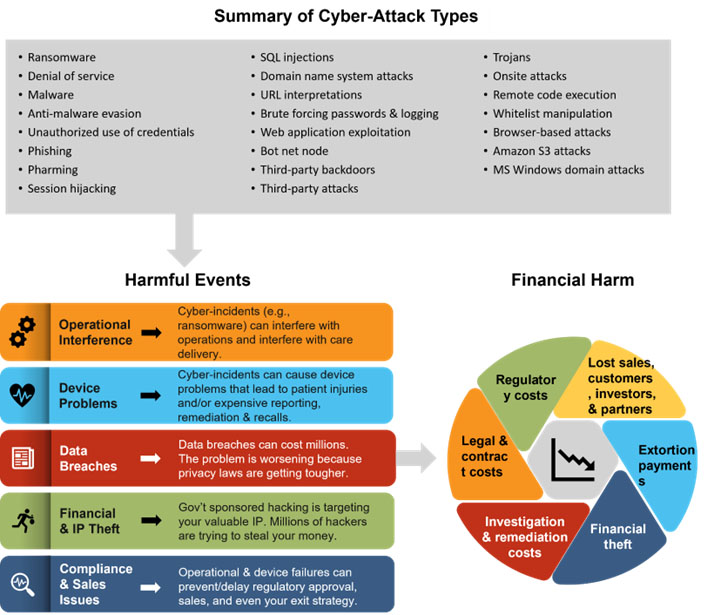
You don’t need a working knowledge of the cyber-attacks in the top gray box of the figure above. But you should know that the following:
- Cyber-attacks can cause one or more harmful events.
- Harmful events can inflict one or more types of financial harm.
- Cyber criminals are quickly and continuously finding new vulnerabilities (as this NIST graph on CVSS Severity over time shows), developing new cyber-attacks, and crafting new ways to use cyber-attacks to make money.
- To cost-effectively mitigate these risks, you need a multi-tool, multidisciplinary cyber risk mitigation system — as our third article in this series will explain.
The following summarizes the harmful events that medtech companies can suffer from cyber-attack, and the related financial harms.
Harmful Event Categories
1. Operational Interruptions: An example is the June 1, 2020, ransomware attack on the University of California San Francisco that encrypted data in its School of Medicine for which the institution paid a $1.14 million ransom. The school also incurred significant investigation costs and untold harm from reputational damage. A reputable cybersecurity company, Sophos, reported that “ransomware attacks on healthcare almost doubled in 2021 (66% in 2021 versus 34% in 2020)” and that “the average remediation cost went up from US$1.27M in 2020 to US$1.85M in 2021.” However, these costs underrepresent represent the long-term damage from reputational harm that can be business-threatening to digital medtech companies. The year 2022 might be even worse, because from January to June, HHS’s Office of Civil Rights, the agency’s investigatory and enforcement arm, reported “256 hacks and information breaches, up from 149 for the same period a year ago.” And the most expensive attack against a medtech/pharma company was the 2017 NotPetya debacle at Merck, for which the company publicly reported that the attack inflicted about $1.3 billion in damage.
2. Device Problems: As we use the term, device problems come from both cyber-incidents that exploit cyber vulnerabilities and just from the existence of those vulnerabilities. Just the existence of vulnerabilities can prevent premarket device approval, interfere with postmarket sales, and/or inflict significant postmarket costs from remediating device vulnerabilities, reputational harm from notifying the public about vulnerabilities, and business-threatening recalls. All these can come with huge costs.
Medtech companies face even greater financial risks when cyber-incidents exploit device vulnerabilities that lead to patient harm. In these instances, the liability is virtually unlimited. According to the e-book “Healthcare Security Woes Balloon in a Covid-Era World,” in 2020, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued more than a half-dozen warnings for infusion pumps and the FDA issued a series of warnings advising medical device manufacturers to secure their devices against various vulnerabilities, including Log4Shell, SweynTooth, URGENT/11, Ripple20, and SigRed. The Ripple20 vulnerabilities are an example of a common, scary, and potentially devastating medical device vulnerability. With new technologies and new devices come new means by which vulnerabilities can be exploited. Consider this NIST chart showing the rapid growth in computing vulnerabilities from 2001 to 2022. (For more information about medtech computing vulnerabilities, try this helpful white paper from Medcrypt.) Moreover, there is a robust plaintiffs’ bar with the resources and expertise ready to bring class actions and individual suits against medtech companies whose devices harm people.
3. Data Breaches: Examples include the 218 million accounts stolen from Zynga in 2019, the 538 million accounts stolen from Sina Weibo (the Chinese Twitter) in 2020, the 162 million user accounts stolen from Dubsmash in 2018, and the 150 million user accounts stolen from My Fitness Pal in 2018. Even one of the ultimate tech companies, Microsoft — with almost unlimited security resources — suffered a data breach of 250 million customer records in 2019. Medtech and healthcare providers suffer data breaches at alarming rates. Consider perusing the many breach investigations by HHS’s Office for Civil Rights, which shows 650 data breaches affecting 500+ individuals in 2020 and 714 in 2022. Data breaches cost companies millions. The Ponemon Institute’s well-respected report stated that the average United States data breach in 2020 cost $8.64 million. Additionally, smaller breaches like the 1.12 million records stolen from Washington State University in 2019 inflict business-killing damage. Washington State had to pay $4.7 million to settle a class action brought by the data breach victims, and in 2015, the primary teaching hospital for the UCLA school of medicine settled its data breach lawsuit for $7.5 million.
4. IP & Financial Theft: Digital medtech companies are prime targets for intellectual property theft. This includes the IP theft by foreign government-sponsored attackers, particularly the Chinese, that the U.S Intelligence Director warned about in December 2020. He said that the “intelligence is clear: Beijing intends to dominate the U.S. and the rest of the planet economically, militarily and technologically.” He described China’s approach of economic espionage as “rob, replicate, and replace,” saying that “China robs U.S. companies of their intellectual property, replicates the technology, and then replaces the U.S. firms in the global marketplace.” Moreover, this IP theft is the primary goal of Hafnium, the cyber-attack group in China responsible for the Microsoft Exchange Server hacks, as discussed below.
5. Sales, Partners, & Compliance Issues: Two of the biggest cyber risks for medical device companies are problems and delays in device approval related to premarket cybersecurity requirements and inability to prove your device’s cybersecurity to customers and partners — who often apply more stringent cybersecurity requirements than the regulators. Digital medtech companies need to understand the market demand for their security, including how they will answer the questions in the Manufacturer Disclosure Statement for Medical Device Security (MDS2), which many large healthcare providers will require before buying your devices. Plus, when setting their cyber risk mitigation strategies, medtech companies need to consider the true potential cost of their cyber risks — which covers all premarket and postmarket costs — which this article helps them do. Another form of partner cyber risk arises through your supply chain: e.g., software or hardware that you incorporate in your devices have computing vulnerabilities that require expensive remediation and/or lead to device malfunctions that injure patients.
Financial Harm Types
1. Lost Sales, Customers, Investors, & Partners: These comprise the costs when harmful event(s) lead to the loss of sales, customers, investors, and partners. In many situations, medtech companies will be required to notify people and/or regulators about the harmful events:
- HIPAA Covered Data Breaches: Many medtech companies are covered by the HIPAA, and the HIPAA Breach Notification Rule, 45 CFR 164.400-414, requires notification to HHS and the public following a breach of unsecured protected health information.
- Data Breaches for Public Companies: The SEC requires public companies to provide notice about any cyber-incident, including data breaches, that meet the materiality standard. In March 2022, the SEC proposed even more stringent data breach reporting requirements.
- FDA Required Reporting: The Medical Device Reporting (MDR) regulation (21 CFR Part 803) requires device manufacturers to report to the FDA when they learn that any of their devices may have caused or contributed to a death or serious injury. The FDA’s Postmarket Management of Cybersecurity in Medical Device guidance requires that device manufacturers report uncontrolled residual risks relating to cyber-incidents and/or cyber vulnerabilities.
- Non-Healthcare Privacy Laws: The GDRP and every state has a privacy law that might require notification.
Therefore, after almost every material cyber-incident your company experiences, your prospects, customers, investors, and partners will find out what happened. In many situations, learning about your cyber-incident will degrade others’ confidence in you in ways that cost you sales, customers, investors, and partners. Much worse are device problems that injure patients, as these harmful events can decimate your reputation and produce staggering liability via class actions or individual lawsuits.
2. Investigation & Remediation Costs: These comprise your costs to investigate the cyber-attack that caused the harmful event(s) and to remediate your operations and/or offerings to at least their original form. These costs can be quite high. As noted above, Sophos found that “the average remediation cost [for healthcare companies hit by ransomware] went up from US$1.27M in 2020 to US$1.85M in 2021.” An additional major financial risk is that some computing vulnerabilities — even if never actually exploited by a cyber-incident — will be so egregious that the FDA will require expensive remediation and/or recalls.
3. Legal & Contract Costs: These comprise your costs from harmful events breaching existing contracts (e.g., SLAs) and/or leading to lawsuits against you. Many medtech companies fail to consider these costs when setting their cyber risk strategies. To avoid this, as article 3 will explain, medtech companies need to deploy a multidisciplinary approach to cyber risk mitigation.
4. Regulatory Costs: These comprise the costs when any relevant regulatory entity investigates your cyber-incident, takes negative actions against you (e.g., fines or enforcement action), and/or requires your company to remediate the harm from a cyber-incident. There’s a slight overlap with investigation and remediation costs, though companies that have cyber-incidents will almost always have investigation and remediation costs but not necessarily regulatory costs.
5. Extortion Payments: These are the costs of paying ransom to cyber-attackers for the means to restore your operations and/or prevent the distribution of information stolen from you.
6. Financial Theft: These are the direct monetary losses when an attacker steals money from you.
4 Factors Exacerbating Cyber Risks
Unfortunately, as this infographic below introduces, four factors are significantly exacerbating medtech’s cyber risks:
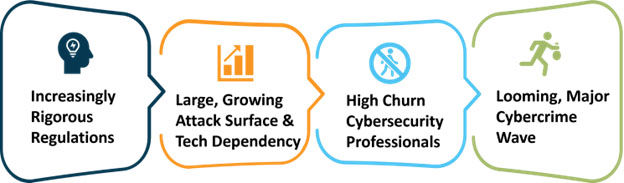
Increasingly Rigorous Regulations: Regulators in the United States, the EU, and around the world are continuously making their medical device cybersecurity requirements more rigorous. The prime examples are EU’s regulations on medical devices 745/2017 (MDR) and on in vitro diagnostic medical devices 746/2017 (IVDR), both adopted and entered into force on May 25, 2017. The MDR took full effect on May 26, 2021, and the IVDR on May 26, 2022. A good explanation of these more rigorous medical device requirements can be found in the MDCG 2019-16 Guidance on Cybersecurity for medical devices.
In April 2022, the FDA published a draft “premarket cybersecurity” guidance that supersedes its 2018 draft premarket cybersecurity guidance. The guidance covers all devices that contain software, firmware, programmable logic, and Software as a Medical Device (SaMD). Highlights of this more rigorous regulatory scheme include:
- Increased emphasis on how cybersecurity relates to the FDA’s Quality System Regulation (QSR), including recommending the use of Secure Product Development Frameworks (SPDF) to achieve that goal. The SPDF comprises all aspects of a device’s total product life cycle, including development, release, support, and decommission.
- Recommendations that the design process include threat modeling be performed in the design process: e.g., how cyber-attackers could attack the device and how the manufacturer would prevent such attacks.
- Recommends a Software Bill of Materials (SBOM) instead of a Cybersecurity Bill of Materials (CBOM). FDA states that the SBOM should include software component descriptors (name, version, manufacturer), level of support provided, end of support date, and any known vulnerabilities.
- While it removed the requirement for manufacturers to categorize their product into risk tiers, it requires them to provide much more detail in their premarket submissions, including providing technical manuals that healthcare providers can use to efficiently patch device vulnerabilities.
While the new draft guidance is voluntary, the FDA does state, “not following the guidance will create greater, probable complexities or potential hardships as far as addressing questions that will come up during the review process. That means potential delays.” This makes it essentially and practically “involuntarily voluntary.”
Large, Growing Attack Surface & Computing Tech Dependency: By their nature, medtech companies strive to innovate and reduce costs by continuously adding more computing technologies, particularly in these areas:
- Increased computing power/internet access and new software applications and hardware to deliver their innovative offerings.
- The dissolution of the traditional security perimeter through cloud storage, mobile devices, and medtech systems in patients’ homes.
- Sophisticated data analytic technologies (e.g., machine learning and AI) needed to disrupt markets and overcome incumbents.
Each addition of computing technology heightens a company’s cyber-attack risks by increasing both its cyber-attack surface (i.e., the sum of physical and digital vulnerabilities that can be exploited to carry out a cyber-attack against you) and its dependency on computing technologies. Unfortunately, the attack surface and dependence on computing technologies of today’s digital medical device companies is enormous and growing at a dangerous time: namely, the looming, major cybercrime way explained below. This stark reality, in addition to other factors, strongly favors incorporating multidisciplinary cyber risk mitigation strategy into your product development process and use of any computing technologies, as article 3 will explain.
High Cybersecurity Professional Churn: The average tenure of chief information security officers (CISOs) in all industries is 26 months, according to the Nominet CISO Stress Report. This churn is a serious problem, both creating high talent search fees and leaving the companies less protected compared with reliable, long-term cybersecurity leadership. Consider these “Cybersecurity Workforce Demand” facts and the 2021 Cybersecurity Workforce Study.
Major, Looming Cybercrime Wave: The economic incentives for cyber criminals are the highest in history, are growing, and are about to generate an unprecedented wave of extortion-based cybercrime, often referred to as ransomware. Most digital medical device leaders understand ransomware basics – namely, that upon infection, it uses encryption to incapacitate computers followed by a payment demand for the means to restore operations, or even destructive action to render a device useless (e.g., NotPetya). But few leaders know that the recent trend of paying ransoms has created a vibrant ransomware ecosystem that even includes the sale of ransomware software-as-service platforms that come with free trials and tech support. Combined with the rapid increase in the use of computing technologies around the world, this vibrant ecosystem is about to generate an unprecedented wave of extortion-based cybercrimes exactly when academic institutions have scant money for security/prevention and keep losing cybersecurity personnel at the highest rate ever.
Moreover, cyber-attacks are becoming ever-more sophisticated, such as the recent Solarwinds debacle and Microsoft Exchange Server hacks. In early 2020, attackers hacked Solarwinds’ software development environment and installed a sophisticated cyber-attack tool (called a backdoor) in the update to Solarwinds’ widely used IT monitoring software. By updating their Solarwinds software, customers installed a backdoor that allowed the attackers to install additional malware and launch more attacks. Because the overall Solarwinds attack was so sophisticated it went undetected for months; compromised the computing systems of at least 18,000 Solarwinds customers, including Fortune 500 companies, many U.S. government agencies, and some universities and colleges, and no one knows the extent of the damage.
In early January 2021, cybersecurity experts learned that cybercriminals were actively exploiting four newly discovered vulnerabilities in multiple versions of Microsoft Exchange Server — email and calendaring software widely used around the world. These vulnerabilities helped the attackers steal information and install additional attack tools that facilitate long-term access to the victim’s computing networks. According to Microsoft VP Tom Burt, the main cybercriminal group exploiting the vulnerabilities, known as Hafnium, is a “highly skilled and sophisticated” “state-sponsored” group operating from China that “primarily targets entities in the United States” to steal “information from a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.” While Microsoft on March 2, 2021 released “security updates” to address these vulnerabilities, the attackers had a long time to use the vulnerabilities to steal valuable information and install covert attack tools. Moreover, according to RiskIQ, 82,731 instances of this software remained insecure (i.e., not updated) as of March 11, 2021. Finally, Microsoft believes that it took about 1,000 software engineers just to create the Solarwinds attack, a massive criminal effort.
The Solarwinds debacle and the Microsoft Exchange Server hacks, therefore, emphasize the gravity of the cyber risks for medtech.
A Realistic Cyber-Attack Scenario
For this cyber-attack scenario, we created a fictitious but realistic medtech company, device, and cyber-attack. The scenario represents an amalgam of companies, devices, and attacks and any resemblance to real companies, devices, or attacks is unintentional.
The Company & Its Device: ACME Company developed and, with FDA approval, commercialized a device, “Less Depressed.” It is implanted in the brain to monitor the neurotransmitters relating to depression (norepinephrine, serotonin, and dopamine), identify patterns relating to depressed feelings/moods, create a customized system to relieve a patient’s depression, and implement the customized system by triggering the release of the appropriate neurochemical in the right dose at the right time. The device comprises (1) a sophisticated implant with a CPU, firmware, memory, and Bluetooth connectivity; (2) an extensive back end comprising powerful machine learning software, and (3) mobile apps with a dashboard that allows patients and their caregivers to see in real-time what is happening. At the time of the attack, Less Depressed was embedded in 10,000 patients around the United States.
The Cyber-Attack
The cyber-attack has three parts:
Infiltrating the development environment: The attackers sent emails to the company’s software developers with appealing attachments containing a malicious reconnaissance trojan that, when opened, gave the attackers access into the development environment. It only took one opening of the malicious email attachment to give the attackers access to — and the ability to covertly study — the software development environment.
The data theft and malicious app update: The attackers used their access to the development environment to do the following:
- identify and copy unencrypted protected health information (PHI) from a database being updated; and
- create a backdoor that allowed them to upload a fake/malicious app that when installed gave them the ability to communicate with and control the apps/devices and terminate the company’s ability to communicate with and control the apps/devices.
The malicious app gave the attackers the ability to (among other things) render the devices forever inoperable (known as “bricking”) through a malicious Bluetooth update; shut down the devices; and even cause the devices to malfunction in ways that harm patients.
Their extortion demand: After verifying that almost all the Less Depressed apps installed the malicious update, the attackers demanded that the company pay them $15 million in Bitcoin within 48 hours; otherwise, they would simultaneously publish the PHI on the web and “brick” all the devices via the Bluetooth attack. Because the attackers terminated the company’s ability to communicate with and control the apps/devices — and gave the company only 48 hours to pay — the company’s defensive options were severely limited. The best defense would be to instruct each of the 10,000 patients individually to uninstall the app, which would not be feasible in 48 hours. This put tremendous pressure on the company to pay the $15 million.
Whether to pay the ransom is a complex, difficult decision, which our next article will cover. In this realistic scenario, the company decided that instead of paying, it would race to shut down all the devices and face the consequences. Its experts convinced the company that paying the ransom was not guaranteed to stop the threat.
What Happened: Unfortunately, in the 48 hours, the company couldn’t regain control of its devices because the company couldn’t reestablish communications with them. That meant they had to instruct patients to delete the Less Depressed app and not reinstall it. Their efforts to communicate with patients within the 48-hour period led to only 5,000 patients deleting the malicious app. Therefore, because they didn’t pay the ransom, the attackers used the malicious Bluetooth update to “brick” the other 5,000 devices, rendering them permanently inoperable and requiring surgeries for each of the 5,000 affected patients to remove them. We estimate that each surgery and follow-up care would cost about $50,000 without any pre-negotiated discounts. We also assume that while abruptly shutting down the devices could have unforeseen dangerous consequences, none arose in this scenario.
The Financial Harm From The Cyber-Attack: The following summarizes the financial harm.
The Investigation & Remediation Costs: The company dropped everything to immediately investigate what happened and try to remediate their computing environment to stop further attacks and harm to the devices and patients. This type of cyber forensic investigation and remediation requires extensive expertise, is very expensive, can be very time consuming, and is far beyond most medtech companies’ internal resources. To even have a chance of success, the company would need immediate access to a team of well-trained cyber forensic experts — something that very few medtech companies have arranged in advance. So, assuming they had such access, the company would need to hire a large team of expert investigators and pay a premium for immediate action: e.g., five people costing $2,000 per day for two days totals $20,000 for just the first 48 hours. Almost assuredly, the company would need to continue the investigation and remediation beyond the first 48 hours. We estimate that just the overall cost of investigation and remediation for this cyber-attack would exceed $300K and be as high as $1 million.
The Legal, Regulatory, & Contract Costs: The company would be required to notify HHS about the PHI data breach and the FDA about the attack on the device and the related vulnerabilities. The company would also be required to notify the patients and the public. This attack, therefore, would likely trigger FDA and HHS investigations. This means that the company would likely need to hire two different expensive outside attorneys: one specializing in FDA investigations and the other specializing in OCR (Office of Civil Rights) investigations. Each investigation could lead to expensive fines, and the FDA investigation might lead to an even more expensive recall. We estimate the following costs:
- Legal fees of at least $150K
- Regulatory fines of at least $100K
- Recall costs of at least (insert cost of surgeries) plus something for the other 5,000 devices.
Additionally, the company might incur significant liability for having to indemnify other entities involved in providing Less Depressed to patients — such as hospital systems and other healthcare providers — that incurred costs because of the attack – including the astronomical amount of $250 million for the surgeries (5,000 x $50K per surgery). There also might be contractual provisions that enable customers to rescind their purchasing agreements.
The greater potential financial harm comes from the inevitable lawsuits, particularly a class action or multidistrict litigation. These suits could be brought by the patients and/or the impacted healthcare providers, and the plaintiffs’ bar is well-prepared and funded to bring these suits. Just defending these actions might cost between $15 million and $20 million, and settling them might include the cost per surgery ($50K) and $100K in damages per plaintiff. The total might be as high as $770 million: $20 million in defense costs plus $750 million in damages ($150K for 5,000 plaintiffs).
Lost Sales, Customers, Investors, & Partners: Because this attack will be public — including many of the details, such as the devices being vulnerable and bricked, the surgeries, and the likely costs — almost all customers, prospects, partners, and investors will know about it. This knowledge would likely do the following:
- Decimate future sales.
- Enable existing customers and partners to cancel all purchase and/or distribution agreements.
- Stop investors from further supporting the company.
This financial harm alone might bankrupt the company, even if the company had excellent insurance that covered a lot of the other financial harm (see the next section), which is unlikely based on the insurance coverage typically bought by medtech companies.
Special section on insurance: To briefly introduce some of the insurance issues, consider the following:
- Any costs paid by health insurers would likely trigger indemnification actions against the company for reimbursement.
- A typical cyber liability policy would cover the ransom payment, investigation, legal costs limited to the data breach and regulatory actions, regulatory fines, and third-party privacy liability claims. Some might cover lost revenue, but that coverage will often have strict limits and exceptions.
- But the company would need strong professional coverage (e.g., technology professional and medical professional liability policies) to cover any of the costs relating to the lawsuits and health insurer indemnification claims.
In a separate article we will explain the insurance issues in more detail.
Bottom-Line Total Estimate: The total potential financial harm from this realistic scenario is mindboggling:
- Investigation and remediation: $300K
- Legal, regulatory, and contract costs (not including lawsuits): $1.25 million.
- Cost of lawsuits: $770 million.
- Lost sales, customers, investors, and partners: bankruptcy
Few, if any, medtech companies could survive this.
Unrealistic optimism about the financial impact of a cyber-attack often leads to medtech companies being woefully underprepared for such attacks. At times, an effective antidote is a “motivational” exercise where you quantify the financial harm from worst-case scenarios for each type of harmful event. A shortcut is to adapt our realistic cyber-attack scenario to your business model and have a multidisciplinary team — finance, operations, sales/marketing, IT, legal, and risk management — collaborate to estimate the financial harm from worst-case scenarios of harmful events. Contact the authors for more information about this valuable exercise.
Conclusion
In the aggregate, cyber risks represent one of the largest financial threats to digital medical device companies. Unfortunately, too many digital medical device companies are using a traditional, technology-centric approach to cyber risk mitigation that is more expensive and less effective than profit-centric, multi-tool, multidisciplinary cyber risk mitigation. Our next article, therefore, helps device manufacturers understand the deficiencies of the traditional cybersecurity model and introduces a more effective approach.
 About The Authors:
About The Authors:
Elliot Turrini is the CEO of Practical Cyber, a cybersecurity and privacy firm with a medtech specialty. He has been a federal cybercrime prosecutor, a cyber/privacy lawyer, and digital health entrepreneur. He is the co-editor of the book Cybercrimes: A Multidisciplinary Analysis.
 Ben Locwin is a healthcare futurist and medtech executive, working to bring the future of better healthcare technology within reach of all patients in need. He has provided oversight to trials of COVID-19 treatments and top vaccine candidates and participates as a member of several state and federal public health task forces. He has spent the last few years working on solutions for cybersecurity issues impinging on medical device regulatory approvals and safe commercial use.
Ben Locwin is a healthcare futurist and medtech executive, working to bring the future of better healthcare technology within reach of all patients in need. He has provided oversight to trials of COVID-19 treatments and top vaccine candidates and participates as a member of several state and federal public health task forces. He has spent the last few years working on solutions for cybersecurity issues impinging on medical device regulatory approvals and safe commercial use.
