Life Sciences Cybersecurity Incident Management: The End-to-End Approach
By John Giantsidis, president, CyberActa, Inc.

Life sciences companies are focusing on smart manufacturing, digital supply chain, and leveraging artificial intelligence (AI)/machine learning (ML) across the value chain, from improving drug discovery in R&D to predictive maintenance and streamlining of manufacturing processes. It is crystal clear that connecting to the world not only brings great opportunities but also generates new risks. Cybercrime is big business and even the smallest malicious attack can seriously damage an organization’s reputation, productivity, and intellectual property (IP) rights. No life sciences organization should think it is safe from cybercrime. Cybercriminals do not just target large finance or banking organizations. On the contrary, a life sciences, medical device, or healthcare organization may be a more lucrative victim because of the information it processes or even the partners it works with. Consequently, the protection of life sciences data, managing third-party and supply chain risks, and planning the retirement of data-rich legacy systems must be prioritized.
A well-designed cybersecurity incident management approach can help shield a company’s operations and ensure that it will be able to utilize the benefits provided by digital technology in every domain of its business. Cybersecurity incident management is not a linear process; it’s a cycle that consists of preparation, detection, incident containment, mitigation, and recovery. Many organizations may not have the necessary in-house expertise and skills to respond adequately to a cybersecurity incident. When they are facing an incident, they may need to call upon experts to contain the incident and/or to carry out forensic investigations. This does not mean that they cannot do anything themselves. On the contrary, there are a lot of things that can and should be done before an actual incident occurs. Drawing up an organization’s cybersecurity incident response is an important first step in cybersecurity incident management. It is also crucial that senior management validates this plan and is involved in every step of the cybersecurity incident management cycle.
It is important to know that one day your organization could be the target of a cyberattack. And when that happens, you need to be prepared. A good cybersecurity incident response plan can make the difference between a cybersecurity incident and a cybersecurity crisis.
There are several basic principles that you should always keep in mind:
- There is no simple one-size-fits-all solution: Every organization is different. What will work for your organization will depend on its mission, goals, data, information, and infrastructure you are protecting.
- Senior management’s commitment: Cybersecurity incidents are a risk that should be incorporated in the overall risk management policy of your organization. Managing cybersecurity incidents does not just mean applying more technology. It also requires the development of a plan that is integrated into the existing processes and organizational structures, so that it enables rather than hinders critical business functions. Therefore, senior management should be actively involved in defining an organization’s cybersecurity prevention and incident response plan, because such explicit support through appropriate internal communication, allocation of personnel and financial resources is key to the success of the plan.
- Involve every member of your organization: Humans are the weakest link when it comes to cybersecurity. Nevertheless, it is also important to realize that the members of your organization have great potential to help you detect and identify cybersecurity incidents. Make sure that every member of your organization is aware of your cybersecurity incident response plan and of their own role within it.
Preparing For A Cybersecurity Incident
Draft a Cybersecurity Incident Response Plan and Keep it Up To Date
When facing a cybersecurity incident, an organization should be able to react in a prompt and appropriate manner. This is why it is important to decide how you will handle certain situations ahead of time instead of when you encounter them for the first time during an incident. Draft a formal written plan to limit damage, to reduce costs and recovery time, and to communicate with both internal and external stakeholders.
Review Your Cybersecurity Incident Response Plan
A cyber incident response plan is not a static document. It is important to integrate it into your business processes and to review and update it regularly, on a yearly basis and as part of the post-incident review.
Cybersecurity Incident Response Procedures
Building on your cybersecurity incident response plan, you can define a number of standard operating procedures for common incidents that are likely to occur within your organization. Such procedures should explain step by step how a specific issue can be tackled. These quick response guides for likely scenarios should be easily accessible.
Content Of A Cybersecurity Incident Response Plan
Know What to Protect
Identify your assets and potential threats.
When hit by an incident, the first questions that will arise are: which assets are at risk and which of those assets are vital for your business activities? You will have to decide which assets need your attention first in order to remain in business and keep the damage to your business as minimal as possible.
That’s why it is crucial to identify, document, and categorize your organization’s “vitals”: the assets your organization depends on to conduct its core activities. This will help you identify where to apply which protective measures and to take quick and justified decisions during the incident management process.
The following list gives you an idea of what those vitals could be: management, organization, processes, knowledge (e.g., intellectual property has been stolen), people, information (e.g., data sets have been stolen or altered), applications (e.g., website is down or defaced), infrastructure (e.g., system and/or network connections are down), and financial capital.
Know How to Identify, Document, and Categorize
- Identify the business and the resources that need to be protected.
- Determine which of your core business activities enable your organization to exist and achieve its corporate objectives and generate income: produce goods, sell goods, deliver goods, etc.
- For each of those activities, identify which systems (databases, applications, control systems) and network connections are supporting them.
- Determine where these systems are located: on your own servers or in the cloud?
- When identifying these assets, don’t forget flows of information to third parties (suppliers, clients, etc.) or industrial control system flows.
- Determine which assets, data, processes, or network connections are so important for your organization that if you lose (control of) them, you are in big trouble or even out of business.
- Assign business priorities for recovery.
- This act of prioritizing will determine the order in which the systems will be reestablished. In most cases, the underlying network will need the highest priority, as this is not only the path by which your system administrators reach your assets but also the path that cybercriminals use to attack your systems. As long as criminals can use your network connections, any other recovery activity might be undone by them. When assets are equally high priority, parallel recovery activities might be considered.
Creating a Cybersecurity Incident Response Team
It is important that the roles and responsibilities in case of a cybersecurity incident are documented in your incident response plan. Start by asking the following questions:
- Who is the internal contact point for cybersecurity incidents? How can he/she be contacted?
- What are the different incident response tasks? Who is responsible for doing what?
- Who is managing the incident from the business/technical side?
- Who will liaise with senior management?
- Who can engage the external incident response partner?
- Who can file a complaint with law enforcement/inform the regulatory bodies?
- Who is entitled to communicate with the press and external parties?
In an ideal world every organization has an incident response team that is convened whenever there is an incident. Of course, the size of the company determines the size and structure of the incident response team. Smaller companies that do not have the resources for an actual team could designate a cyber first responder – ideally someone with business decision capability – from among their personnel.
Different skills are needed to take on the different responsibilities and necessary roles in an efficient incident response; see Table 1 as an example. For smaller companies, some of these skills may have to be outsourced.
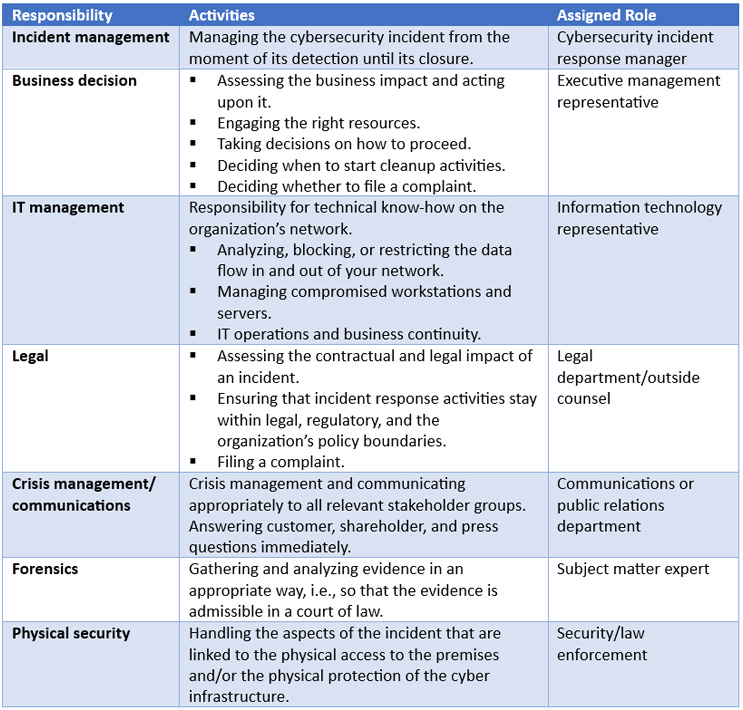
Table 1: Cybersecurity incident management roles
Preparing Your Communication Strategy
Communication is a vital component of every step in the cybersecurity incident response. You want to control the communication flow to ensure the right information is communicated at the right moment by the right senders to the right recipients. This is valid both for internal communication and communications to the outside world.
What to Communicate and with Whom
The type of incident and its (potential) impact will define the type of communication that is required. For example, a hacking attempt will most likely not warrant communication with the media to disclose the incident. All communications should strike the right balance between transparency and protection and, in most cases, internal communication will be more transparent than external communication. Even for internal communication, however, a need-to-know principle should be respected.
During the incident response activities, there will be a constant need for information from many different stakeholders. Each of them will need a different type of information. Compile your own list of stakeholders; see Table 2 as an example, and ensure that the right contact information is available.

Table 2: Stakeholder communication matrix
Once you’ve established who you will communicate with and what you will tell them, you need to decide when you will contact them. The timing should be based on the communication’s objectives. Timing is important:
- Some stakeholders will need information as soon as possible because they can help contain the cybersecurity incident (e.g., your organization’s top management, employees).
- Other stakeholders (e.g., national authority, or sector-specific agency) have to be contacted within a certain legally imposed time frame.
- Others (e.g., media) may contact you and in such a case you should have your answers ready.
It may be necessary to instigate a no-communication phase from the moment the incident is detected until the moment when you have a full picture of the incident and an action plan. If the perpetrator is alerted, they will probably retreat and erase all their tracks or, even worse, do some additional final damage. Organizations should bear in mind that once a party has been informed, they will request periodic updates related to the incident in question. There is typically no one-off communication and the communication schedule should take these periodic updates into account.
Conclusion
The experience of suffering a cyber incident should not be the impetus for better cyber preparation. Every organization should be well-prepared to manage a cybersecurity incident. An effective cyber incident management is primarily a business activity that can be driven by executive management. The prevalence of cyber threats in the modern life sciences environment makes it critical for boards of directors and senior executives to take an active interest in how their organization will respond to and manage an incident and having the mechanisms or mitigating controls in place to prevent similar incidents in the future.
About the Author:
 John Giantsidis is the president of CyberActa, Inc., a consultancy for heavily regulated industries and sectors, headquartered in Boston, MA, offering global data-driven digital, regulatory, cyber, and privacy solutions. He is the vice chair of the Florida Bar’s Cybersecurity and Privacy Law Committee and a Cyber Aux with the U.S. Marine Corps. He holds a Bachelor of Science degree from Clark University, a Juris Doctor from the University of New Hampshire, and a Master of Engineering in cybersecurity policy and compliance from George Washington University. He can be reached at john.giantsidis@cyberacta.com.
John Giantsidis is the president of CyberActa, Inc., a consultancy for heavily regulated industries and sectors, headquartered in Boston, MA, offering global data-driven digital, regulatory, cyber, and privacy solutions. He is the vice chair of the Florida Bar’s Cybersecurity and Privacy Law Committee and a Cyber Aux with the U.S. Marine Corps. He holds a Bachelor of Science degree from Clark University, a Juris Doctor from the University of New Hampshire, and a Master of Engineering in cybersecurity policy and compliance from George Washington University. He can be reached at john.giantsidis@cyberacta.com.
