Medical Device QMS Cybersecurity: Threat Modeling
By John Giantsidis, president, CyberActa, Inc.

Healthcare is increasingly dependent on digital services and connected medical devices, leading to an increase in cyberattacks, primarily due to the value of data that can be obtained. Regulations play a key role in defining cybersecurity requirements and adopting cybersecurity and data protection related measures. The FDA has been involved in medical device cybersecurity since the 2000s and is moving forward with its overhaul of its medical device cybersecurity expectations. In an earlier article, I provided a detailed evaluation of FDA’s latest guidance, highlighting all the areas and actions that a medical device manufacturer will need to address.1 In this article series, I will detail and expand upon on how to best “teach” your QMS cybersecurity. In Part 1, I will discuss the fundamental activity of threat modeling. Part 2 will cover how to best implement security by design in your organization. I will examine the integration of security risk management into the medical device risk management program in Part 3. Lastly, in Part 4, I will go through the steps to plan, execute, report, and act upon penetration testing and vulnerability scanning, how to interpret the results, and how to prioritize your efforts.
The FDA considers threat modeling fundamental in your premarket submission and expects you to include system level risks in its creation and deployment. As such, it would have to cover design, production, and supply chain. But how do we go about threat modeling for our device? And how do we build the requisite QMS infrastructure and processes?
Threat modeling is a structured process for identifying threat events that are pertinent to your medical device so you can build the appropriate defense to protect it during design, production, deployment, and use. Figure 1 illustrates the general steps associated with threat modeling.

Figure 1. Threat Modeling Steps
Let’s take a closer look at each step.
Scope Identification
It is important to establish the technical scope, system architecture, and system components before performing threat modeling for your medical device. It is strongly suggested you also examine the security perimeters, interfaces, and data flows to characterize the attack surface. The information pertaining to the system architecture and dependencies can be found through the instructions for use (IFU) manual, software design document (SDD), technical specification, or any system-related documentation. A key activity, which is usually bypassed, it to interview the product managers, engineering, quality, regulatory, and other pertinent personnel to get their input on the medical device architecture.
System Decomposition
System decomposition is the process of breaking down a medical device into its different components. Components refer to external entities, users, processes, or data stores, thereby establishing an understanding of the data flows among the medical device components. Constructing a data flow diagram (DFD) can bring insights to the operation of a medical device by providing a visual representation that shows how the “nuts and bolts” of the system work. A DFD is exceptionally useful in identifying how data moves through the medical device or system in question. System decomposition comprises three easy steps:
Step 1: Identify System Components
Identify medical device components prone to attack, i.e., the components that a potential attacker may be interested in, categorized as follows:
- data or functions essential to the business mission of the system; and
- data or functions that are of special interest to an attacker.
Step 2: Data Flows
Once medical device system components have been identified, map out how the components communicate with one another or provide some form of access to one another. With a completed DFD, you will be able to visualize how data flows through the medical device and which components are involved.
Step 3: Trust Boundaries
A trust boundary can be used to represent the change of trust levels as the data flows through medical device. The trust boundaries provide you with the various intersections of data flow, which helps to identify attack surfaces.
Threat Identification
Threat identification is simply a systematic method to identify threat events relevant to your medical device, comprising identifying threat vectors and documenting threat events. One common approach that can be used in this step is the STRIDE methodology, using NIST SP 800-302 for threat sources and events. A great resource for threats related to web applications is the OWASP Automated Threat Handbook.3 It is strongly recommended that medical device manufacturers join the Health Information Sharing and Analysis Center4 (Health-ISAC) to obtain complimentary information from additional threat intelligence sources. Since threats are constantly evolving, it is important to leverage threat intelligence sources to gain knowledge on the latest threats, learn how attackers may target your devices, and implement the appropriate actions.
Step 1: Identify Threat Vectors
Threat vectors are paths that an attacker can exploit to penetrate a medical device component or bypass its overall defenses. As such, utilizing the previously generated DFD, you will be able to identify threat vectors to your medical device by applying vulnerability studies and current intelligence on threat actors.
Step 2: List Possible Threat Events
An attacker may, by means of a vector, act against the medical device to cause harm or steal information. Threat events can be characterized by the tactics, techniques, and procedures (TTP) employed by the attacker. To enumerate all possible threat events, TTPs, and attack sources comprehensively, it is suggested you use methods like STRIDE, security cards, or leverage the draft NIST 800-154, which provides information on the basics of threat modeling for data-centric systems like medical devices.
Attack Modeling
Attack modeling describes an attacker’s intrusion approach so medical device manufacturers can identify mitigation controls needed to defend their device or SaMD and prioritize its implementation. By understanding the attack vectors and security risks at various stages, these models provide useful insights for the user to apply multilayered controls to prevent attacks, interrupt ongoing attacks, and minimize the impact of an attack.
There are several frameworks you can use to perform attack modeling; some focus on the overall asset being modeled (asset-centric), some that focus on the attackers (attack-centric), and some on the software (software-centric). For medical devices and digital health applications, the U.S. National Institute of Standards and Technology (NIST) data-centric threat modeling methodology5 works best because it focuses on protecting high-value health data within healthcare systems. It is simple and has four major steps:
- Identification and characterization of system and data of interest;
- Identification and selection of attack vectors;
- Characterization of the security controls used for mitigation; and
- Threat model analysis.
Another well-established framework that works great for medical devices, SaMD, and digital health applications is Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) by the MITRE.6 The ATT&CK basis provides a comprehensive matrix of tactics and techniques used by attackers to compromise an organization’s system:
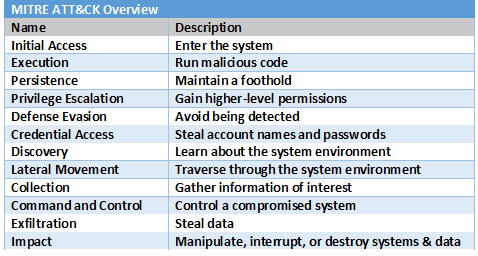
ATT&CK is a dynamic framework as MITRE continually updates and revises the framework with the latest tactics and techniques discovered or disclosed.
Conclusion
The FDA and other regulatory agencies believe threat modeling can play a critical role in addressing risks posed by medical devices and having better, more rigorous threat modeling is now expected in premarket submission packets. Threat modeling documentation can ultimately demonstrate how the risks were assessed and controls implemented for the system to address questions of safety and effectiveness. This article elaborated on threat modeling and provided practices and a systematic way for medical device manufacturers to derive a robust system threat model process that can be adopted into your existing QMS.
Part 2 will cover how to best implement security by design in your organization. I will examine the integration of security risk management into the medical device risk management program in Part 3. Lastly, in Part 4, I will go through the steps to plan, execute, report, and act upon penetration testing and vulnerability scanning, how to interpret the results, and how to prioritize your efforts.
References
- https://www.meddeviceonline.com/doc/fda-releases-guidance-on-cybersecurity-in-medical-devices-0001
- https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/final
- https://owasp.org/www-pdf-archive/Automated-threat-handbook.pdf
- https://h-isac.org
- https://csrc.nist.gov/CSRC/media/Publications/sp/800-154/draft/documents/sp800_154_draft.pdf
- https://attack.mitre.org/
About The Author:
 John Giantsidis is the president of CyberActa, Inc., a boutique consultancy empowering medical device, digital health, and pharmaceutical companies in their cybersecurity, privacy, data integrity, risk, regulatory compliance, and commercialization endeavors. He is the vice chair of the Florida Bar’s Committee on Technology and a Cyber Aux with the U.S. Marine Corps. He holds a Bachelor of Science degree from Clark University, a Juris Doctor from the University of New Hampshire, and a Master of Engineering in cybersecurity policy and compliance from The George Washington University. He can be reached at john.giantsidis@cyberacta.com.
John Giantsidis is the president of CyberActa, Inc., a boutique consultancy empowering medical device, digital health, and pharmaceutical companies in their cybersecurity, privacy, data integrity, risk, regulatory compliance, and commercialization endeavors. He is the vice chair of the Florida Bar’s Committee on Technology and a Cyber Aux with the U.S. Marine Corps. He holds a Bachelor of Science degree from Clark University, a Juris Doctor from the University of New Hampshire, and a Master of Engineering in cybersecurity policy and compliance from The George Washington University. He can be reached at john.giantsidis@cyberacta.com.
